How to get ephemeral access keys to an AWS account using MFA

As engineers, we often find ourselves writing automations that interact with our AWS environment via CLI, infrastructure as code, or Python scripts.
Programmatic access makes it easier to automate tasks like cloud deployments, application upgrades, learning new AWS services, running migration scripts, cloud configuration analysis, incident response, and infrastructure maintenance.
That ease of development access, however, comes at a cost. Having programmatic access turned on all the time in an organization requires a vast set of Identity and Access Management (IAM) permissions that, without proper controls in place, may present too much risk.
This post shows how you can overcome those risks by enumerating AWS best practices on access keys management.
Common security risks with IAM access keys
- Cryptojacking: Usage of access keys to utilize cloud compute resources to mine cryptocurrencies.
- Data exfiltration: Once access keys are compromised, data resources or compute resources with access to those might be compromised as well depending on the perimeter of IAM profile. If access keys have a role that enable editing AWS Lambda and the lambda has access to RDS instance, this instance data can be compromised.
- Malicious activity: An over permissive access key can grant access to shut down instances and cause downtime to an application.
AWS IAM credentials best practices
AWS IAM is a crucial service used to grant and restrict access to AWS services and resources securely. To get programmatic access, we need to apply IAM best practices such as:
- A user must perform an MFA challenge to get such a level of access.
- Programmatic access must be temporary. That way, if AWS access keys do get leaked into a public git repository or unencrypted log, they will exist only in the short-term and will automatically expire after a few hours.
- Requests for keys should integrate with our identity provider as a source of allowed users.
- Roles must be controlled and monitored via AWS CloudTrail.
- Roles should follow least-privilege principles, and the tool should allow you to choose which role to use, assuming each role grants a different level of access.
With these requirements in mind, there are three services that can help us:
- onelogin-python-aws-assume-role: Assume an AWS Role and get temporary credentials using OneLogin.
- Gimme AWS Creds: A CLI that utilizes an Okta IdP via SAML to acquire temporary AWS credentials via AWS STS.
- AWS SSO: AWS SSO enables developers to sign in directly to the CLI using the same Active Directory or AWS SSO credentials that they normally use to sign in to AWS SSO and access their assigned accounts and roles.
Getting ephemeral access keys
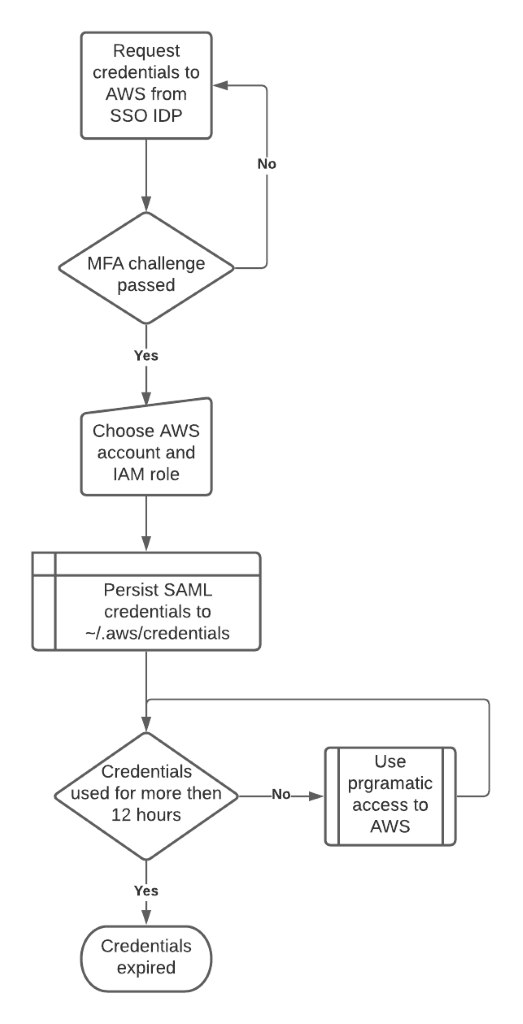
After installing one of the above tools, you can now begin to obtain access keys. I set up onelogin-python-aws-assume-role and then started the process of obtaining temporary access keys described in the following diagram, with modified session duration to 12 hours.
Let’s run it step-by-step:
First, request AWS credentials by running:
You will then be prompted to answer the MFA challenge:
If the challenge is passed, you then select your AWS account and IAM role:
Override the AWS default profile with new temporary credentials located at ~/.aws/credentials:
Now you can run AWS CLI commands using those credentials for the following hours.
Supporting multiple AWS Organizations
One of the challenges with this approach is integrating several multi-role and multi-account configurations under several separate OneLogin applications.
This kind of configuration allows us to have multiple levels of SSO apps segregation in our organization. A typical example would be: having an SSO application for multiple dev AWS accounts and roles, with a separate SSO application for production accounts.
To enable just that, we made an open source contribution which is currently available on a GitHub fork, with a pull request open pending feedback. Using our contribution, you will be able to get time-bound access keys using SAML and an MFA application that you’re familiar with, such as OneLogin.
Following least-privilege roles in AWS
Allowing temporary roles solves a portion of the possible risk related to access. To follow least-privilege principles means that only the required access level is granted to those who need it when they need it. On an existing AWS account, we might find orphaned AWS IAM roles that are no longer in use and over-privileged roles, which can be restricted by modeling the actual usage.
To solve this next part of the puzzle, we created AirIAM, an open source tool that helps identify unused and over-privileged IAM roles.
Get similar stories in your inbox weekly, for free
Share this story:

Bridgecrew
Bridgecrew is the cloud security platform for developers. By leveraging automation and delivering security-as-code, Bridgecrew empowers teams to find, fix, and prevent misconfigurations in deployed cloud resources and in infrastructure as code.
Latest stories
Best Cloud Hosting in the USA
This article explores five notable cloud hosting offers in the USA in a detailed way.
Best Dedicated Hosting in the USA
In this article, we explore 5 of the best dedicated hosting providers in the USA: …
The best tools for bare metal automation that people actually use
Bare metal automation turns slow, error-prone server installs into repeatable, API-driven workflows by combining provisioning, …
HIPAA and PCI DSS Hosting for SMBs: How to Choose the Right Provider
HIPAA protects patient data; PCI DSS protects payment data. Many small and mid-sized businesses now …
The Rise of GPUOps: Where Infrastructure Meets Thermodynamics
GPUs used to be a line item. Now they're the heartbeat of modern infrastructure.
Top Bare-Metal Hosting Providers in the USA
In a cloud-first world, certain workloads still require full control over hardware. High-performance computing, latency-sensitive …
Top 8 Cloud GPU Providers for AI and Machine Learning
As AI and machine learning workloads grow in complexity and scale, the need for powerful, …
How ManageEngine Applications Manager Can Help Overcome Challenges In Kubernetes Monitoring
We tested ManageEngine Applications Manager to monitor different Kubernetes clusters. This post shares our review …
AIOps with Site24x7: Maximizing Efficiency at an Affordable Cost
In this post we'll dive deep into integrating AIOps in your business suing Site24x7 to …
A Review of Zoho ManageEngine
Zoho Corp., formerly known as AdventNet Inc., has established itself as a major player in …