As reported in the 2020 IBM X-force report, retail is now the second most targeted industry after finance in cyberattacks. This is now being compounded by large efforts led by hackers that profit on the current turbulent times.
An increase in e-commerce during the crisis?
In these turbulent times, a lot of conflicting data is circulating. Some sources claim that e-commerce is currently booming - due to people staying at home and avoiding physical stores. Others say that it is likely to decline.
Nevertheless the data is hardly surprising. Some sectors and niches in retail will probably stand a lot to gain, while others most likely will lose. Customer preferences change quickly in recessions or in turbulent economies. But regardless of which - attackers tend to take advantage of the turbulent times and overwhelmed companies.
The attacker
The most common type of hackers targeting retail organizations are financially motivated cybercriminals, who target the industry to obtain consumers personally identifiable information, payment card data, financial data, shopping history, and loyalty program information. Cybercriminals typically use this data to take over customers accounts, defraud customers, and reuse the data in various identity theft scenarios.
In the meantime more people than ever are working from home, often with fewer security defenses and more general distractions making them more vulnerable to different kinds of attacks. Thus making consumers more likely to fall for malicious scams and tricks.
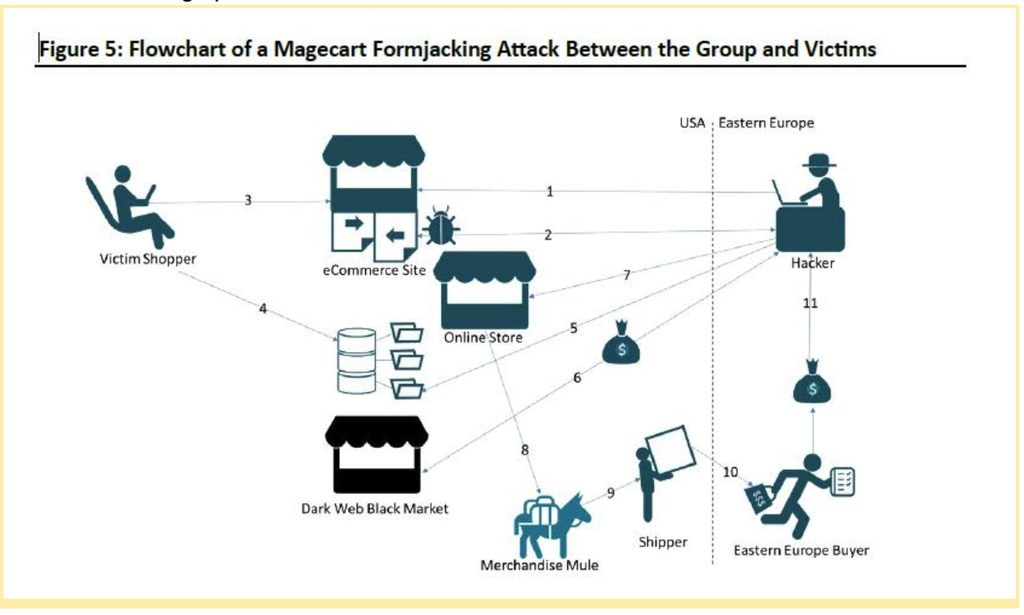
Magecart - an elaborate example of what can happen
The card skimming attacks enabled by Magecart have already been used successfully to infiltrate and steal card data from more than 100,000 e-commerce sites.
“Magecart is "an umbrella term given to at least seven cybercriminal groups that are placing digital credit card skimmers on compromised e-commerce sites at an unprecedented rate and with frightening success,"
- security firms RiskIQ and Flashpoint said in a report issued last year.
In short, the attacks are carried out by injecting Javascript code into the forms used on checkout-pages and payment forms.
After the customer data is skimmed it is used to purchase expensive electronics from other stores. Then, goods are sent by mules to eastern europe - therefore making tracking and retrieving the goods virtually impossible. The goods are then sold with high margins and the hackers make large profits.
“A major concern is that many companies are not updating and patching their web applications, or not checking if the code has been tampered with by attackers,” said Aaron Lint, chief scientist and vice president of research at Arxan, in an interview with Security Media Group.
Even the largest were affected
Magento was the primary third-party shopping software targeted, inspiring the now-infamous name, which is a combination of “Magento” and “shopping cart.” To this day, third-party shopping platforms such as Magento and OpenCart, which fuel an enormous portion of e-commerce, are the lifeblood of many Magecart groups.
Besides Magento, and thereby all companies using them as their e-commerce platform, famous brands such as Amazon and British airways were also affected.
What can you do to protect your business?
As always there is no clear-cut answer. But there is a clear distinction between mainly relying on a finished platform, if you have built your own or heavily modified an existing one.
If you are using a finished platform, your best bet is to keep the version of your platform as updated as possible as many attacks use known vulnerabilities to exploit systems on mass-scale. The next step is probably to make sure that the configuration of your website is not introducing any potential weaknesses for an attacker to use. A low hanging fruit is to make sure that you are using HTTPS, still a remarkable amount of websites in 2020 do not.
If you have heavily modified your platform and introduced a lot of custom code, then your next step should be to evaluate both the code that you have written, but also potential dependencies/open source components introduced. As mentioned above, known vulnerabilities are often exploited and are the second most common attack-vector according to IBM research. Often in the form of different plug-ins and tools.
For evaluating your code and deployment environment the OWASP-Top 10 framework could be useful. It helps you analyze the following most probable security risks in your software:
- Injection.
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting XSS
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging & Monitoring
How can you automate this?
The task of going through all the OWASP Top 10 security risks can be quite daunting. Probably, you would need external help by professionals to do it thoroughly if you don't have a week of spare time.
To the rescue comes tools such as Debricked, Detectify, Foreseeti, Burp-suite and others that on their own can test for the different risks. Together they can become a strong combination in your software development routine and cybersecurity management. Check their respective websites to read more about them individually.
We at Debricked can help you scan for vulnerabilities in the third party components / dependencies / plugins and open source software that you use within your e-commerce platform.
We also provide training & education on topics such as OWASP Top 10 that can help you create developer awareness on cybersecurity within your company.
Get similar stories in your inbox weekly, for free
Share this story:

Debricked
Debricked is a Swedish tech start-up on a journey to secure open source, one dependency at a time.
Latest stories
Best Cloud Hosting in the USA
This article explores five notable cloud hosting offers in the USA in a detailed way.
Best Dedicated Hosting in the USA
In this article, we explore 5 of the best dedicated hosting providers in the USA: …
The best tools for bare metal automation that people actually use
Bare metal automation turns slow, error-prone server installs into repeatable, API-driven workflows by combining provisioning, …
HIPAA and PCI DSS Hosting for SMBs: How to Choose the Right Provider
HIPAA protects patient data; PCI DSS protects payment data. Many small and mid-sized businesses now …
The Rise of GPUOps: Where Infrastructure Meets Thermodynamics
GPUs used to be a line item. Now they're the heartbeat of modern infrastructure.
Top Bare-Metal Hosting Providers in the USA
In a cloud-first world, certain workloads still require full control over hardware. High-performance computing, latency-sensitive …
Top 8 Cloud GPU Providers for AI and Machine Learning
As AI and machine learning workloads grow in complexity and scale, the need for powerful, …
How ManageEngine Applications Manager Can Help Overcome Challenges In Kubernetes Monitoring
We tested ManageEngine Applications Manager to monitor different Kubernetes clusters. This post shares our review …
AIOps with Site24x7: Maximizing Efficiency at an Affordable Cost
In this post we'll dive deep into integrating AIOps in your business suing Site24x7 to …
A Review of Zoho ManageEngine
Zoho Corp., formerly known as AdventNet Inc., has established itself as a major player in …