7 Kubernetes Security Scanners to Use in Your DevSecOps Pipeline
in Kubernetes , Orchestration , DevSecOps

Advanced security of your cluster is one of the downsides of Kubernetes that requires serious attention. Attackers can take advantage of a loophole or misconfiguration in a Kubernetes cluster to exploit your application environment and probably force you out of business.
Thankfully, there are third-party, free and open source Kubernetes security tools developed to help scan your cluster and identify potential loopholes before it’s being exploited.
With the growing number of organizations using Kubernetes as an orchestration tool due to its flexibility and other benefits, clusters' security is becoming more vulnerable.
Even though Kubernetes provides basic IAM and role-based access control (RBAC) roles to secure the system, they are too basic and does not meet the security requirements of modern application and system breaches are on the rise like never before.
To address this issue and improve Kubernetes clusters' security, many organizations have developed free open-source and paid solutions that can scan Kubernetes clusters, identify issues, and propose a suitable solution to the problem.
Let’s take a look at some of them in this article.
Kubeaudit
Kubeaudit is a Golang written command-line tool developed by Shopify. It audits Kubernetes clusters by comparing them against some predefined security tests called “auditors.” It tests the Kubernetes cluster against a list of auditors, such as whether there are loopholes that allow privilege escalation, whether there is a misconfiguration in any cluster image, the SecurityContext of the pods, or whether the root account is disabled for the system or not.
It doesn’t only audits the cluster for vulnerabilities but also gives recommendations on how to solve them. Each “auditor” provides comprehensive details and best practices to apply in your system. The tool also encourages that your applications are run as a no root user, that the root filesystem is given read-only access, and other general security practices.
Kubeaudit performs its audit in three modes: Manifest, Local and, Cluster, and reports the result as Error, Warm, or Info according to the level of severity of the found issue.
It can be installed via Homebrew by running a single command: brew install kubeaudit or run as a kubectl plugin using: kubectl audit.
Kubesec
Kubsec is an open-source Kubernetes security scanner and analysis tool. It scans your Kubernetes cluster for common exploitable risks such as privileged capabilities and provides a severity score for each found vulnerability.
It takes a single Kubernetes YAML manifest file input. It can be installed on your system using container image, its binary package, or used as a kubectl plugin to scan the Kubernetes deployment, pods, and resources. You can also run Kubesec-as-a-Service via HTTPS at v2.kubesec.io/scan.
Kube Bench
Kube Bench is used for running tests in Kubernetes to ensure compliance with the Center for Internet Security, CIS’s best practices. CIS is a regulatory body that provides guidelines and benchmark tests for writing secure and standard codes.
Kube Bench is an open-source tool from Aquasecurity that checks if your Kubernetes cluster meets the CIS benchmarks. It highlights the areas of your Kubernetes environment that don’t comply with CIS benchmarks and also provides suggested solutions to resolve them.
It is a Golang application that is deployable as a container. The tests are easily extensible and defined in YAML with support for JSON format output. This makes it easy to run Kube Bench in managed Kubernetes services such as Amazon Elastic Kubernetes Service (EKS) and OpenShift.
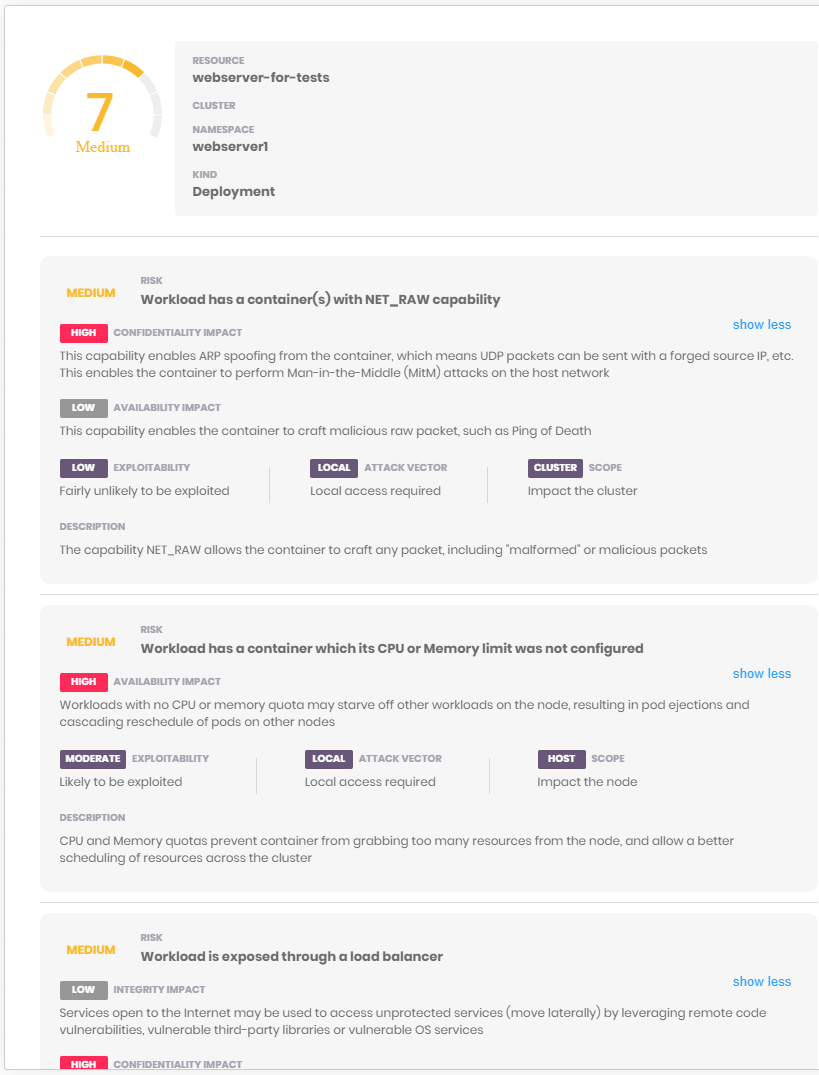
Kube Scan
Kube Scan is an open-source Kubernetes risk scanning tool that scans and scores clusters from 1 to 9; the higher the number, the higher the risk. The score and details of risks are presented in a web UI. The risk score is calculated based on the Kubernetes Common Configuration Scoring System (KSCCSS) framework.
KCCSS is an open-source framework that uses various Kubernetes security settings such as Kubernetes policies, capabilities, and privilege levels to create a risk baseline used to generate a risk score.
Kube Scan is a container scanner that runs as a container in the cluster and rescans the cluster every 24 hours to provide up-to-date, actionable risk data.
Kube Scan’s KCCSS list can be extended to suit your specific rules and run as a command-line utility.
Kube Score
Kube Score is a tool used for performing static code analysis of Kubernetes object definitions. It then provides a list of suggestions and recommendations of what can be done to improve your application security as the output.
Kube Score uses a non-intrusive method to scan object definitions without causing any harm to the system. It outputs its error messages and risk resolution instructions in a human-readable form, making it easy to understand by professionals, thereby making the application more secure, reliable, and resilient.
Kube Score can be used directly from the web at kube-score.com for easy and quick analysis or installed using Docker, Homebrew, Krew, or the prebuilt binaries for Mac, Windows, and Linux.
Kube Hunter
Kube Hunter is another open-source Kubernetes vulnerability scanner created by Aqua Security. This tool goes more profound than the Kube Bench by scanning Kubernetes pods and clusters outside the CIS practices to identify potentially dangerous issues before attackers exploit them.
It further enhances the Kube bench's CIS rules with discovery and penetration testing capabilities to hunt down potential security threats in the Kubernetes cluster.
Kube Hunter offers multiple options to run the tool locally by setting it to a remote interface or network scanning. It returns around 40 different vulnerabilities, which come with individual IDs and error messages to make it easy to look up each issue.
KubiScan
Lastly, KubiScan is a Kubernetes security scanner that gives insight into how your Kubernetes environment handles role-based access control (RBAC). It is a command-line tool focused on scanning and identifying potential risks in permissions and roles settings.
The tool allows you to easily search for pods with privileged accounts and invoke calls to query the role associated with specific pods.
How To Choose The Right Kubernetes Security Scanner
Having access to this range of tools can be a little overwhelming to identify and choose which one is right for you.
Firstly, you should understand the ultimate goal of choosing security scanners for your Kubernetes to achieve an efficient, secure, and reliable environment to continue delivering business value for your clients with little or no system downtime.
To achieve this, you need to choose from the array of tools, one that suits your environment and use case.
When choosing your Kubernetes vulnerability scanner, you should first consider how easy and quick it is to set up/install for use. Scanners like Kubeaudit offer an effortless single-line command to install the tool. One that provides a web platform such as Kube Score will make it easy and quick to scan your Kubernetes cluster without installing the scanner locally.
To ensure your application environment complies with a general security benchmark, you can choose Kube Bench or, better still, use it with Kube Hunter for an extensive and deep vulnerability scan.
If you need a straightforward vulnerability scanner that points out the cluster's exact area that has an issue, Kubeaudit is your go-to tool. Also, if what you need is a comprehensive detail of the underlying issues and the solution, Kube Score, Kube Scan, and Kube Hunter are great choices.
The bottom line is that whatever tool you choose is dependent on the need of your Kubernetes environment. You can, however, combine a couple of different scanners to achieve your desired result.
Get similar stories in your inbox weekly, for free
Share this story:

The Chief I/O
The team behind this website. We help IT leaders, decision-makers and IT professionals understand topics like Distributed Computing, AIOps & Cloud Native
Latest stories
Best Cloud Hosting in the USA
This article explores five notable cloud hosting offers in the USA in a detailed way.
Best Dedicated Hosting in the USA
In this article, we explore 5 of the best dedicated hosting providers in the USA: …
The best tools for bare metal automation that people actually use
Bare metal automation turns slow, error-prone server installs into repeatable, API-driven workflows by combining provisioning, …
HIPAA and PCI DSS Hosting for SMBs: How to Choose the Right Provider
HIPAA protects patient data; PCI DSS protects payment data. Many small and mid-sized businesses now …
The Rise of GPUOps: Where Infrastructure Meets Thermodynamics
GPUs used to be a line item. Now they're the heartbeat of modern infrastructure.
Top Bare-Metal Hosting Providers in the USA
In a cloud-first world, certain workloads still require full control over hardware. High-performance computing, latency-sensitive …
Top 8 Cloud GPU Providers for AI and Machine Learning
As AI and machine learning workloads grow in complexity and scale, the need for powerful, …
How ManageEngine Applications Manager Can Help Overcome Challenges In Kubernetes Monitoring
We tested ManageEngine Applications Manager to monitor different Kubernetes clusters. This post shares our review …
AIOps with Site24x7: Maximizing Efficiency at an Affordable Cost
In this post we'll dive deep into integrating AIOps in your business suing Site24x7 to …
A Review of Zoho ManageEngine
Zoho Corp., formerly known as AdventNet Inc., has established itself as a major player in …