An Insight Into How the Conti Gang Targets Microsoft Exchange Servers

We look at how attackers can use PowerShell to orchestrate attacks on vulnerable servers and the need for improved server security. A disgruntled employee leaks modus operandi for a highly successful ransomware syndicate.
Conti is a somewhat new ransomware syndicate appearing in May 2020; they are otherwise known by their alias, the Conti gang and have claimed over 150 successful attacks, which amounts to millions of dollars in fees that have been extorted from victims. The Conti gang makes attacks on encrypted data located on an infected machine. They are famous for their double-extortion technique, in which they first demand a ransom in exchange for a decryption key. This is followed by a threat to release the encrypted data in their possession.
They drive home a threat by showing a small portion of the data and requesting that ransom be paid to prevent total leakage. Asides from encrypting their victims' data, the ransomware gang makes use of a multithreading technique which gives them a unique ability that quickly spreads their coverage within an infected network. Thereby, makes them difficult to stop and allows them even further encrypt more files on other hosts within the network via the servers.
An affiliate who has claimed to be shortchanged after a deal with the gang has since leaked a playbook that the ransomware gang uses for its operations.
Analyzing the attacks has since revealed that the assailants first gain access to particular organizations with ProxyShell. This is a prototype of the method used by the Epsilon Ref ransomware gang, the ProxyLogon attack in May, this has become a rising method by ransomware gangs, and they are quickly gaining confidence in their experience.
ProxyShell is used to gain access to these organization websites and set up a remote shell. Within a short time, the ransomware gang would have obtained a list of the network's computers and their domain controllers and administrators. Seven back doors were created, including two web shells, four commercial remote access tools, and a Cobalt strike. They used this to gain access and carry out a highly sophisticated attack.
This list would then give them access to the credentials of domain administrators, and they begin to execute commands.
This trick was noted and studied by Sophos on ProxyShell based attacks by one of Conti's affiliates.
Since these attacks were first noticed, Microsoft has made fixes to mitigate the vulnerabilities. Users, however, need to upgrade to a recent Exchange server, an update that may result in email downtime, and several companies are yet to make updates. This still leaves them at risk of these attacks.
Looking at examined cases
In this case, examined by Sophos labs, the target’s Windows 2012 R2 Standard server had been operating the Exchange Server 2016 cumulative update 3.
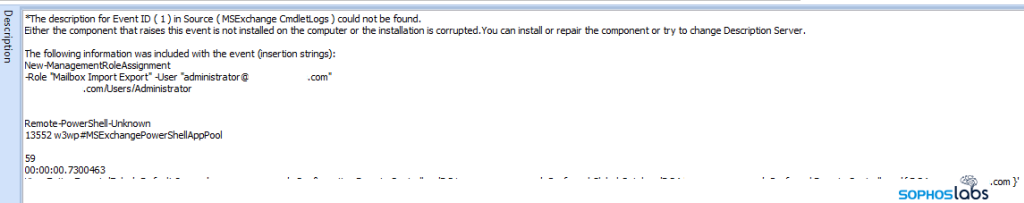
The assailants had used ProxyShell to create a new mailbox and had it assigned “administrator,” and then gave roles to that mailbox using Microsoft Exchange “cmdlets”. These assigned roles included the rights to execute PowerShell commands remotely.
This is shown in the images above.
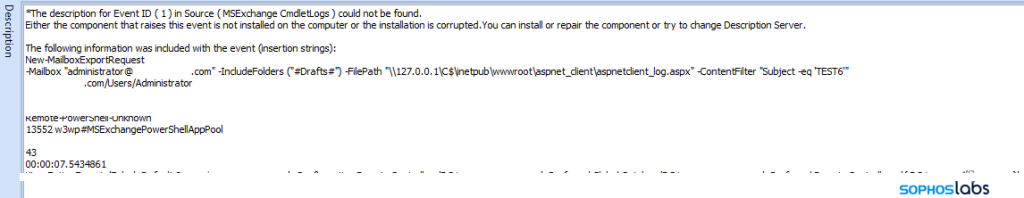
A different case showed how a mailbox referencing "Evil Corp" was created as a part of the attack
And after securing access, they created a web shell on the localhost address of the server:
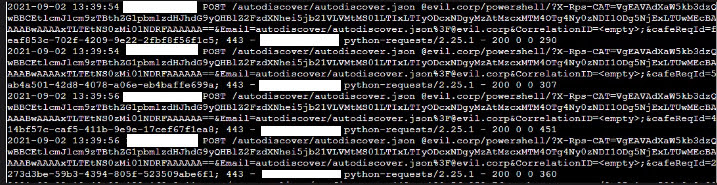
\\127.0.0.1\C$\inetpub\wwwroot\aspnet_client\aspnetclient_log.aspxSubsequent attacks were noticed by first issuing a PowerShell script encoded in base64.
A series of commands were issued varying in intensity that led to the abuse of the service control manager and execution of a directory lookup on the directory where the web shell was dropped.
You can find a series of these commands in the article that Sophos news released on Conti affiliates.
It shows how the intruders gained strong access that allowed them to exploit the vulnerable exchange server.
The impact the attack had
The resulting impact the attack had was a loss of access to data. The attack was thoroughly carried out by complete documentation of the victim's network even before the gang made the initial move.
This greatly reduces the chances of discovering the ransomware's presence as it was operated from servers instead of operating from individual machines.
However, these attacks have pointed out the need for organisations to increase security and prevent malware and update their servers.
Several tools used by the Conti gang for the operation were obtained from the Sophos lab web page.
Ransomware attacks to come In the future
And seeing that quite a number of companies are yet to upgrade their Microsoft exchange servers, these attacks might get frequent fast.
However, ransomware gangs have been in hiding with crackdowns from international authorities, and mounting pressure to eradicate them keeps increasing. Some big names have even been nipped, Revil and DarkSide among them.
Several new groups have been noticed; however, this may or may not directly result from the recent breakdown of larger organizations. But a large bet is being placed on these smaller groups being spawns of them. They are already searching for large organizations that can pay them millions of dollars in ransom when attacked.
Get similar stories in your inbox weekly, for free
Share this story:

The Chief I/O
The team behind this website. We help IT leaders, decision-makers and IT professionals understand topics like Distributed Computing, AIOps & Cloud Native
Latest stories
How ManageEngine Applications Manager Can Help Overcome Challenges In Kubernetes Monitoring
We tested ManageEngine Applications Manager to monitor different Kubernetes clusters. This post shares our review …
AIOps with Site24x7: Maximizing Efficiency at an Affordable Cost
In this post we'll dive deep into integrating AIOps in your business suing Site24x7 to …
A Review of Zoho ManageEngine
Zoho Corp., formerly known as AdventNet Inc., has established itself as a major player in …
Should I learn Java in 2023? A Practical Guide
Java is one of the most widely used programming languages in the world. It has …
The fastest way to ramp up on DevOps
You probably have been thinking of moving to DevOps or learning DevOps as a beginner. …
Why You Need a Blockchain Node Provider
In this article, we briefly cover the concept of blockchain nodes provider and explain why …
Top 5 Virtual desktop Provides in 2022
Here are the top 5 virtual desktop providers who offer a range of benefits such …
Why Your Business Should Connect Directly To Your Cloud
Today, companies make the most use of cloud technology regardless of their size and sector. …
7 Must-Watch DevSecOps Videos
Security is a crucial part of application development and DevSecOps makes it easy and continuous.The …