Highlights From the 2021 State Of API Security Report
in DevOps , Programming , DevSecOps , APIs , CyberSecurity

The report outlines where companies are falling short in protecting their APIs and statistics on security incidents experienced.
API security plays a vital role in ensuring that the organization’s data and applications are protected from unauthorized access. Given that 80% of the internet traffic comes from APIs, it should come as no surprise that this is one of the most attacked points by hackers.
The report indicates that 11% of Salt's customers got more than 500 attacks a month. The assumption that this is a developers’ problem is misguided and there needs to be a change of strategy to improve security. Most organizations are now encouraging collaboration between security and DevOps teams as they seek to close the existing security gaps.
The report by SaltLabs summarizes the current status and views on API security. This report was prepared from the input of over 200 professionals in the field of security, application, and DevOps.
This is a summary of the key takeaways from the Q3 2021 ‘State of API Security’ report.
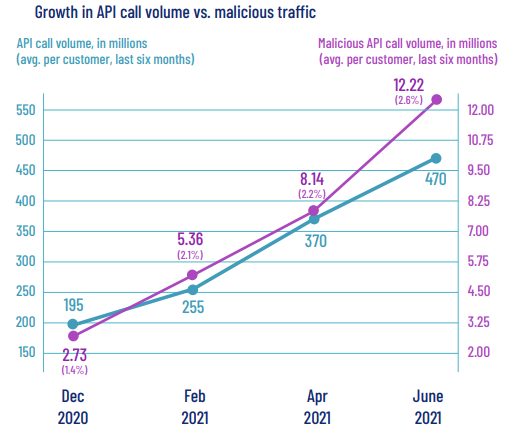
Malicious attacks have increased three-fold
The report indicates that there has been a significant rise in the number of API calls from the start of the year to July of 2021. In the last 6 months of 2020, SaltLabs customers’ API calls totalled 195 million with 1.4% malicious attacks, and six months after it, the API calls totalled 470 million with 2.6% malicious attacks. This shows that as the API calls increased, the number of attacks grew by more than 3 times.
The increase of attacks from 2.72 million to 12.22 million represents a growth rate of 348% within a period of just six months. The data shows that as API usage continues to increase, we can expect to have more malicious attacks.
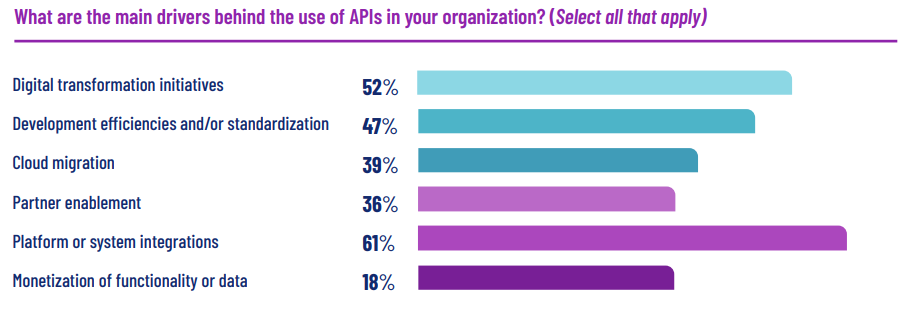
API security concerns are slowing down projects implementation
The report state that 64% of the respondents view security concerns as a challenge in implementing projects that require API integration. This is a big problem for businesses using APIs considering that 61% use it for system integration, 47% for improving efficiency in project implementation, and 52% for digital transformation.
Delays caused by security concerns affect their ability to create the best products within the desired period.
Security challenges are not limited to one stage of development
The data on the report shows that many companies are not fully sold on creating and deploying API due to security issues faced in different stages. 26% of respondents surveyed had no confidence that security could be guaranteed at the pre-production stage. This number is lower at the production stage where only 20% stated they were concerned about runtime security. The lack of confidence in the security systems discourages companies from developing formalized application programs.
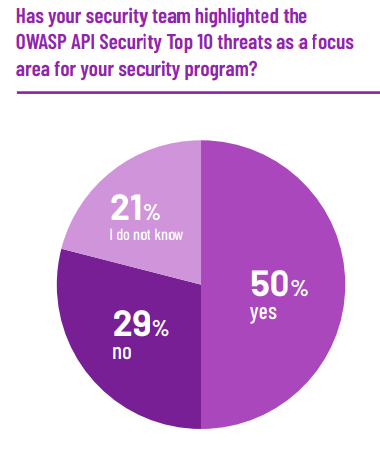
To address the existing security gaps, the report recommends making use of OWASP API Security’s top 10 threats list to understand areas of weaknesses. While 50% of respondents stated that they had used the list, 29% had not used it at all.
Developers cannot be solely responsible for API security
As the number of API attacks increases, the questions on who should bear the responsibility for securing the organization has gained more focus. 57% of the respondents placed the responsibility on three teams, DevOps, API developers, and developers.
The shortcoming of assigning blame and/or responsibility to just one team limits the organization’s ability to respond to future threats.
There are three reasons why developers cannot be slowly responsible for the security: no code is perfect, application development is sometimes fully or partially outsourced, and API also requires runtime protection. This is why a secure API will require coordination of all teams that interact with it from development to deployment and monitoring. This is important, given that 94% of respondents experienced an API security incident in the last 12 months.
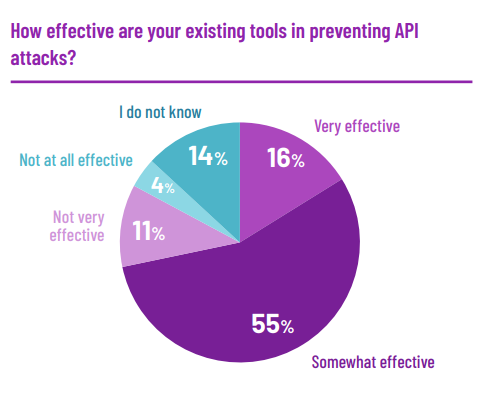
The effectiveness of tools used to identify attacks is questionable
Identifying the attack is a big challenge as only 16% of the respondents stated the existing tools have been very effective. The number of security incidences is likely higher than what is reported given that 12% of the respondents stated that they have no way of identifying an attack.
The two tools used by almost half of the respondents to identify API attacks are WAF and API gateway. The report also disapproves the assumption that the authentication mechanism keeps you safe by stating that authenticated APIs got 95% of the successful attacks while the unauthenticated group got 5% of the attacks.
Security at runtime has the highest priority
According to the reports, 54% of the respondent see stopping API attacks at runtime as the highest priority. The shortage of resources inhibits organizations from deploying strategies that can stop such attacks. This may be why only 38% of the respondents have a robust strategy for securing their APIs. The rest rely on a basic or no strategy despite being aware of the dangers of API attacks.
Frequent API changes are creating an inventory problem
Keeping a detailed and secure inventory of the APIs plays an important role in ensuring there is efficiency in API development. It is therefore worrying that 85% of the respondents did not have confidence with their API inventory. With 60% of organizations changing their APIs every month and 6% changing them every day, keeping an accurate inventory can be a challenge. This problem can be solved by automating API discovery which keeps pace with the changes made.
The frequent API changes increase the number of outdated APIs that continue to persist when they should be deprecated. As per the report, 40% of the respondents ranked it as a bigger problem than account takeover.
Another challenge cited by the report is that 85% of the respondents weren’t sure they know the APIs that expose sensitive data. Knowing the data that the API has or it exposes is very important when deciding where and how to secure it.
Collaboration between security teams and DevOps will lead to increased API security
To help resolve the API security gaps that have persisted for many years 2 out of every 3 organizations are now championing increased collaboration between security and DevOps teams. The increased collaboration is bound to have a greater impact on how API security is implemented in the future.
It is also important for organizations to create robust strategies integrating the latest mechanisms if API security is to be increased.
The report outlines where companies are falling short in protecting their applications and statistics on security incidents experienced.
You may be interested in reading:
How Do Teams Automate Security in 2020?
Top 10 Kubernetes Security Tools
Top 12 Open Source Security Testing Tools
7 Kubernetes Security Scanners to Use in Your DevSecOps Pipeline
Takeaways from The State of Containers and Kubernetes Security
Get similar stories in your inbox weekly, for free
Share this story:

The Chief I/O
The team behind this website. We help IT leaders, decision-makers and IT professionals understand topics like Distributed Computing, AIOps & Cloud Native
Latest stories
How ManageEngine Applications Manager Can Help Overcome Challenges In Kubernetes Monitoring
We tested ManageEngine Applications Manager to monitor different Kubernetes clusters. This post shares our review …
AIOps with Site24x7: Maximizing Efficiency at an Affordable Cost
In this post we'll dive deep into integrating AIOps in your business suing Site24x7 to …
A Review of Zoho ManageEngine
Zoho Corp., formerly known as AdventNet Inc., has established itself as a major player in …
Should I learn Java in 2023? A Practical Guide
Java is one of the most widely used programming languages in the world. It has …
The fastest way to ramp up on DevOps
You probably have been thinking of moving to DevOps or learning DevOps as a beginner. …
Why You Need a Blockchain Node Provider
In this article, we briefly cover the concept of blockchain nodes provider and explain why …
Top 5 Virtual desktop Provides in 2022
Here are the top 5 virtual desktop providers who offer a range of benefits such …
Why Your Business Should Connect Directly To Your Cloud
Today, companies make the most use of cloud technology regardless of their size and sector. …
7 Must-Watch DevSecOps Videos
Security is a crucial part of application development and DevSecOps makes it easy and continuous.The …