ITIL4 and DevSecOps
in DevSecOps

ITIL4 is the newly revamped IT Service Management Framework to accommodate the Industry 4.0 Revolution. Based on the new set of Manuals, ITIL4: High-Velocity IT is the manual which is covering the aspects of DevSecOps, DevOps, SRE.
ITIL4 is the newly revamped IT Service Management Framework to accommodate the Industry 4.0 Revolution. Based on the new set of Manuals, ITIL4: High-Velocity IT is the manual which is covering the aspects of DevSecOps, DevOps, SRE.
“Digital Technology is increasingly important. Its economic, societal, and political impacts are unprecedented. At the same time, it is increasingly challenging for digital practitioners to design, develop, run, and support the systems and services that fulfill this demand. ITIL4 High-velocity IT focuses on digital products and services, including digital customer experiences, covering good organizational practices and mental models, all from a practitioner’s perspective.” – From the HVIT manual from Axelos.
Every organization is a technology company and there is a huge increase in the use of devices, apps, and IoT, etc. Cybersecurity risk is increasing at the same rate or even more. Information is available at the speed of your connection and data breaches are expensive.
We also see that the vulnerabilities that we see are the ones that we are seeing for quite some time. The OWASP top 10 has vulnerabilities at the top for the last 7 years. Gartner predicts that, through 2020, 99% of vulnerabilities exploited will continue to be the ones known by security and IT professionals for at least one year.
Security has become very important and as per DevSecOps, “Security is everyone’s responsibility”. Security needs to be brought into the lifecycle from the time of requirements itself.
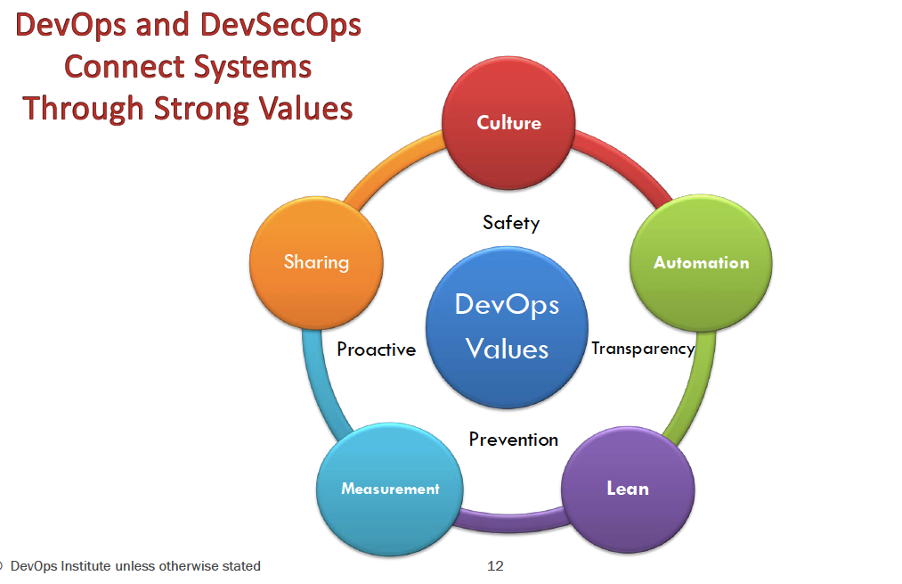
DevOps and DevSecOps connect through a system of strong values. The diagram below shows the values of DevOps and DevSecOps.
What is DevSecOps?
It is not about the name but the concept. Security must be completely integrated with Development and Operations. This is the time to reinvent Security. We need to Leverage Automation, Redefine the roles and practices of Security Engineering, Security Management and Governance, Risk Management and Compliance (GRC). We need to start implementing “Security as a Code” and Security Policies as Code.
GRC and Security SMEs needs to come as trusted advisor to the team. Remember the Project to Product Approach where it is one team looking after all the needs of a set of applications from new changes to maintaining it without the need to go out of the Squad for anything related to capability, skills and decision making.
DevSecOps is getting Security embedded in DevOps. Security team operates in DevOps Manner. Shifting of Security left with Dev and Ops empowering Security.
The New Way
DevSecOps is redefining the way of running a DevOps initiative. We need to focus on the following:
- Incentive Model
- Resilience
- Organizational Culture
- Generativity
- The Advice Process
Resilience
Resilience is about how fast we can get back to normal after an incident or attack. There is nothing called 100% Secure. We need to get back with normal business at the earliest even with a security attack. We need the following to enable that among others:
• Fail Fast, Learn Fast, Recover Fast
• The best way to avoid failure is by failing regularly (Netflix) - Choose where to fail
• Security is important for Reliability and hence for Resilience
• Continuous Experimentation and Learning is important for Security aspects too
We need to be following Lean principles:
- Minimize Overhead and Waste
- Automate as much as possible – People makes mistakes, scripts do not
- Emphasize on measurable results and the outcome effectiveness
- Do not make Rules for the sake of making Rules
- Come as a Trusted Advisor and not as a Road-blocker
It is important to understand the Context and have a holistic view.
The following are important points to keep in mind:
- Context is everything
- Understanding of the business (Domain) is important
- Take a holistic approach
- Level of Tolerance in various service areas (Do not spend 200$ for saving a 5$ Asset)
- Website
- Backend System
- Data
- Understanding of the entire System (System Design)
How much of Security is enough? Security SMEs should come a co-operative partner and not as an adversary. We need to strike a balance between Real Vs. Perceived Threats. Threat Modelling is one of the most important and mandatory technique to follow throughout the lifecycle from the time of Designing. Evaluate Asset Vs Threats Vs Vulnerabilities. Pick your battle.
Here is an example of the STRIDE model for Threat Modelling. There are others available too.
Risk Management with High Velocity IT
In this current high-speed world, we have less time for in-depth analysis. Follow the Laloux’s “Advice Process”. Develop methods for rapid analysis. Understand all the architectures. Design is a very important aspect and Security has to be designed into the system. Understanding of the holistic IT landscape is important. System Design approach will help.
Basic Security Hygiene
There needs to have basic security hygiene for everyone in the Squad. These can be:
- Vulnerability and Patch Management
- Automate Scanning and Report Processing
- Automate Patch Management
- Operations Management
- Backups, Replication and Redundancy – Production like data must have Production like Security
- Monitoring Size and Utilization
- Basic Network Security
- Firewalls
- IDS/IPS (Intrusion Detection System/Intrusion Prevention System
- Remote Access
Logging and Monitoring
Logging and Monitoring for Security is also a very critical aspect. We need to look at the following 3 areas:
- Log Management
- Incident Response
- Threat Intelligence
The following are some of the activities related to the above 3:
- Setting Up Log Management
- Central Repository
- Queries/Reporting/Alert – One Alert for One Service
- Opportunities for Automation
- Incident Response and Forensics
- Upskill - Cloud Skills
- Live Information and Response
- Serverless
- Containers
- Leverage Automation Opportunities
- Data Capture
- Enrichment activities after Alert
- Automate workflow for Forensic Analysis
- Have Contingency Plan – (Nothing is 100%)
- Call for help
- Pre-define Incident Response Plan
- Chaos Engineering and Fire Drills
- Threat Intel and Information Sharing
ITIL4 – High-Velocity IT
Now that we understand Security, let us see what ITIL4 has got us related to Security and DevSecOps. The following is the IT Value Stack (From ITIL4: High-Velocity IT Manuscript by Axelos):
Objectives of HVIT:
- Valuable Investments
- Fast Deployment
- Resilient Operations
- Co-created Value
- Assured Conformance
Key Characteristics of HVIT are:
- Lean
- Agile
- Continuous
- Resilient
Resilient
HVIT is talking about Resilience a lot. Security comes under this. A system cannot be Reliable if it is not Secure. The following are the different practices and processes helping to incorporate Resilience:
- “Approaches with resilient characteristics are focused on maintaining workable availability and performance, and minimizing the effect of Incidents”. - From Axelos HVIT Manual
- SRE and DevSecOps focuses on reliability and a system cannot be Reliable without being Secure
- As per ITIL4 - HVIT, “Security Officer’s role shifts from specifying requirements and monitoring performance, to enabling practitioners to address security concerns.”
- The practice relevant to Security is Information Security Management and helps in Resilient Operations and Assured Conformance
The following are the various practices and processes related to Security:
- Infrastructure as Code – Designing and Enforcing Security Policies in Virtual Infrastructure components
- Loosely Coupled Architecture – Design and manage Information Security Policies for loosely coupled services and service components
- Blameless Postmortem – Obtaining more information about the circumstances related to security breaches and security incidents.
- Ci/CD – Ensuring compliance with information security policies by reducing manual work. Increasing the scale and scope of automation by leveraging CI/CD tools may help to ensure compliance with information security policies by reducing manual work (TOIL) and improving traceability of changes.
- Continuous Testing (CT) - Here 2 practices are involved. First, Service Validation and Testing – Unit and integration Testing is conducted on an ongoing basis throughout the development lifecycle This includes application unit testing, infrastructure services testing, functional/non-functional testing, canary releases, blue/green testing, and infrastructure security Testing. The next practice is Information Security Management – Ensuring compliance with InfoSec policies by reducing manual work. Leveraging automated testing tools may help to ensure compliance with information security policies by reducing manual work and improving the traceability of changes.
- Technical Debt – Design, implementation and improvement of information security controls are influenced by existing technical debt. Information Security controls can be also result in the creation of technical debt, which needs to be acknowledged and communicated to all relevant stakeholders.
- Use of Tools like Security Monkey
- Non-functional criteria should specify the quality needed by the people who will operate, maintain, and enhance the system, and by those who will ensure security and regulatory compliance.
- Definition of Done - Security Tests such as Vulnerability, Penetration, or policy compliance should be considered in the definition of done for resilient products and services
- Version Control – Addressing or closing information security risks by flagging vulnerable versions of service components
- Security can contribute significantly to relationship management due to better service management
- Assured conformance can be measured by or lack of security breaches, fines by regulators, bad publicity, actions required by internal and external auditors, and the cost of measures to ensure conformance with GRC issues
- Audit Defense Toolkit – Information Security Management – Designing and implementing controls in the product lifecycle to provide extensive traceability and joint accountability. Service Configuration Management – Standard configurations to support security and audit requirements
- Specific section is provided on explaining DevSecOps (Sec 4.5.2)
- Processes supporting Information Security Management:
- Security Incident Management Process
- Risk Management Process
- Control Review and Audit Process
- Identity and Access Management Process
- Event Management
- Procedures for Penetration Testing, Vulnerability Scanning, etc
- Procedures for managing security related changes, such as firewall configuration changes
- The integrated way of approaching security contributes to assured conformance
- DevSecOpsis relevant for the following:
- Continual Improvement – Improvements to security controls and policies can be part of the learning and feedback incorporated by development and operations
- Information Security Management – Designing and implementing controls in a development lifecycle to provide extensive traceability and joint accountability. Integrating Information security duties into the daily work of practitioners. Information Security Management and Risk Management should be an integral part of the daily work of practitioners
- Monitoring and Event Management – Configuring monitoring tools to continually scan for threats and vulnerabilities
- Change Enablement – Implementing a preventative control that automatically requires pre-authorization from security management before developers can make certain types of production data edits
- Deployment Management – Security Management guides on key credential management, CD pipeline security checks, container security, automated pentesting, and data and performance management.
- Knowledge Management – Access to Security Policies
- Risk Management – Security is about Risk
- Service Validation and Testing – Test data management is a key element that helps to ensure continued stability, reliability, availability and security
- Strategy Management – Integrating duties to balance regulatory requirements with speed of execution
- Workforce and Talent Management – Training and Coaching staff and other relevant stakeholders in how to build security into development and operations work
- Business Analysis - Understanding the security policies, standards, risks, potential threats, and vulnerabilities in internal and external environments and translating them into requirements for development and operations team and including security requirements into product backlog
- Infrastructure and Platform Management – Security Management can enhance infrastructure and platform management with guidance on secure standards and training, privacy reviews, threat modelling, credential management and data security, especially with Infrastructure as code
- Software Development and Management – Enhancing software development with guidance on secure coding standards and training, privacy reviews, threat modelling, code analysis, source code and credential management and data security
Finally, I would also like to mention the point from the recent Google SRE book – Build Secure and Reliable Systems where there is a lot of focus on the Designing for Security.
The following are some of the key points:
- As per Google, Security and Privacy are closely related concepts.
- In designing for reliability and security, you must consider different risks. Primary reliability risks are non-malicious like a bad software update or a physical device failure. Security risks comes from adversaries who are actively trying to exploit system vulnerabilities.
- Reliability and Security Tradeoff – Redundancy
- Reliability and Security Tradeoff – Incident Management – Special small team with skills to handle security related incidents
- Security and Reliability is about Confidentiality, Integrity and Availability
- Intersection of Reliability and Security – Effects of Insiders
- Design of Security and Reliability
- Design for least privilege
- Design for understandability
- Design for resilience
- Design for recovery
- Mitigating Denial of Service (DOS) attacks
We should also touch upon the need for Secure Automation as there is lot of automation done everywhere, both in Dev and Ops Side including SRE. Automation protects from chance of human error or willful sabotage and provide secure opportunities. The following points are important:
- Secure Automation
- Automated steps in the pipeline can be secure but manual steps cannot be secure
- Artifacts used in the pipeline can be validated and checked for compliance through digitally versioning and signing
- DevSecOps has introduced security into the build-test-deploy lifecycle
- SRE places extra emphasis on Security in Production
- Secure Build
- Application, Infrastructure and Configuration changes through code analysis tools and check for security issues
- Digitally signed artifacts to avoid “fake” code
- Secure coding practices to share with everyone
- Secure code repositories with proper access control
- Open source product with feedback from community
- Secure Test
- For Infrastructure change in an “immutable” test environments creation guarantees compliance with code repository
- Deploy artifacts on test environment securely
- Test Data and Test scenarios are built for security
- Secure Staging
- Staging environments are immutable
- Same artifact deployed in all environments
- Production like data in any environment needs production like security
- Dedicated Security Scanning
- Proxy Security Requirements to be considered
- Secure Production
- Immutable Production Environment
- Same artifact in Production environment
- Regulatory Compliance needs to be evidenced and best done with automation and observability
- Failure Testing helps audit compliance
There is a great amount of involvement of both Development and Operations in providing a Reliable and Secure System. Security needs to be looked at seriously and everyone should take the Shared Accountability.
SRE Foundation, DevSecOps Courses from DevOps Institute will give more details of each.
To learn more and meet with the experts of DevSecOps across the globe, get your free tickets for the largest DevSecOps event in Asia – Devops India Summit 2020 Virtual. www.devopsindiasummit.com
Get similar stories in your inbox weekly, for free
Share this story:

Xellentro
Xellentro is an emerging global provider of project, program and portfolio management consulting and training services. Established in 2012, with Headquarters in Bangalore, India, Xellentro works closely with its clients in tackling their most difficult organizational development challenges. Xellentro is a specialist organization that works with its clients to identify improvement areas and uses experienced consultants to enhance their business and development processes.
Latest stories
How ManageEngine Applications Manager Can Help Overcome Challenges In Kubernetes Monitoring
We tested ManageEngine Applications Manager to monitor different Kubernetes clusters. This post shares our review …
AIOps with Site24x7: Maximizing Efficiency at an Affordable Cost
In this post we'll dive deep into integrating AIOps in your business suing Site24x7 to …
A Review of Zoho ManageEngine
Zoho Corp., formerly known as AdventNet Inc., has established itself as a major player in …
Should I learn Java in 2023? A Practical Guide
Java is one of the most widely used programming languages in the world. It has …
The fastest way to ramp up on DevOps
You probably have been thinking of moving to DevOps or learning DevOps as a beginner. …
Why You Need a Blockchain Node Provider
In this article, we briefly cover the concept of blockchain nodes provider and explain why …
Top 5 Virtual desktop Provides in 2022
Here are the top 5 virtual desktop providers who offer a range of benefits such …
Why Your Business Should Connect Directly To Your Cloud
Today, companies make the most use of cloud technology regardless of their size and sector. …
7 Must-Watch DevSecOps Videos
Security is a crucial part of application development and DevSecOps makes it easy and continuous.The …