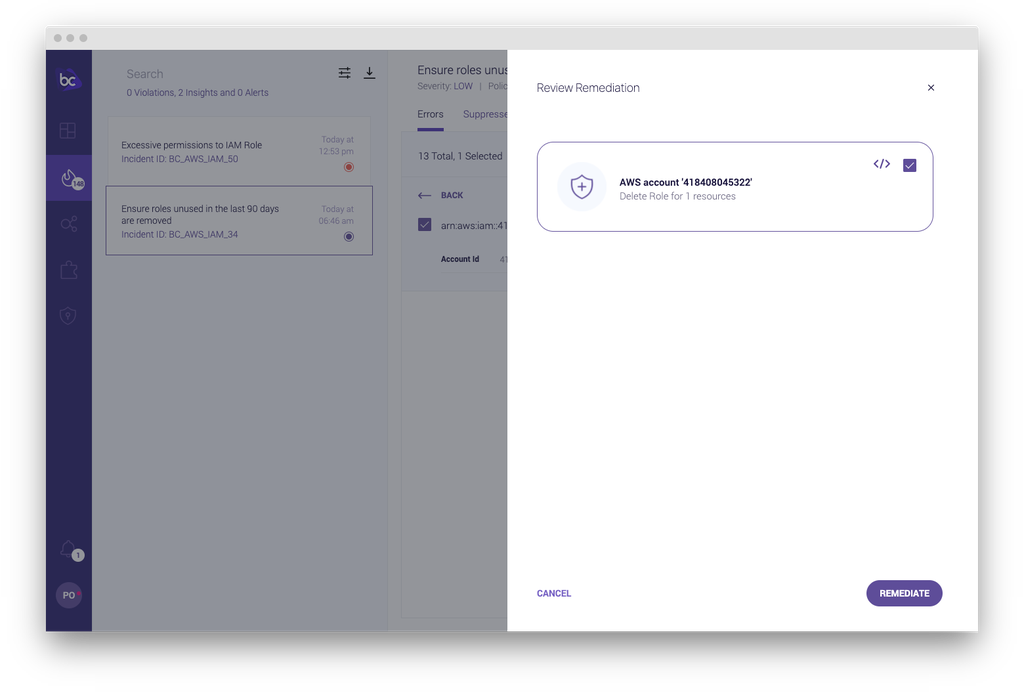
IAM Insights: Automated right-sizing with policy-as-code

AWS Identity and Access Management (IAM) is one of the few services at the backbone of almost every AWS cloud resource, but its importance was often overlooked. In recent years, new community projects and native tooling have cropped up to improve how we build and maintain secure IAM.
Much of the attention on IAM has centered around reducing the vulnerable surface of an IAM configuration by adhering to the principle of least privilege (POLP). In theory, implementing POLP is simple; grant only the permissions required to perform specific tasks.
In practice, however, POLP is challenging to parse across teams as they expand their usage of existing services. That’s because underlying IAM permissions often need to change in order to ensure that every security, infrastructure, and DevOps engineer has the correct permissions they need in a changing environment. AWS has done a great job supporting backward compatibility, but developers have suffered another challenge—forward compatibility. In other words, building fast and innovating in the cloud is often at odds with maintaining least-privilege IAM. The result is either too-generic default policies or overly-permissive defined policies.
Enter Cloud Identity Entitlement Management (CIEM). As recently outlined in Gartner’s 2020 Hype Cycle for Cloud Security, CIEM distinguishes the continuous management of IAM from the broader context of cloud management. In addition to vendors starting to solve for this use case, there are several community-powered projects that provide creative solutions in this problem space:
- CloudMapper by Scott Piper helps create instant visibility to existing IAM settings
- Policy Sentry by Kinard McQuade introduced automated policy generation
- RepoKid and Aardvark by Netflix help materialize dynamic IAM analysis and its benefits for continuous policy right-sizing
In that same vein, we open-sourced AirIAM earlier this year to help developers automatically migrate their existing IAM permissions into a least-privilege Terraform file. Since its release, AirIAM has helped codify thousands of IAM configurations. Leveraging the machine-readability of Terraform enables us to manage IAM just as we would any other configuration, utilizing version control, immutable designs, and git-based review processes. It also opens up other interesting use cases, such as automating IAM drift detection.
In continuing our support for helping teams develop and maintain secure IAM, we’re excited to introduce IAM Insights. By utilizing infrastructure as code and providing developer-friendly workflows, Bridgecrew makes it easier to ensure that permissions across users, roles, groups, and custom policies retain POLP.
How IAM Insights works
As part of Bridgecrew’s all-in-one codified cloud security platform, IAM Insights leverages our existing policy-as-code framework to assess, resolve, and govern risks in AWS IAM.
Continuously assess permissions and patterns
Automated polling processes fetch AWS IAM data from both your code and your cloud to model IAM policy documents and determine usage patterns. Each finding is enriched with additional context derived from Bridgecrew’s resource graph. 
Resolve overly-permissive permissions at the source
Excessive and unused permissions are removed at the policy level, and a new policy document is provided. Fixed policies can then be copied directly into console settings, changed automatically via Lambda, or replaced using a pull request.
Govern IAM policies
By pairing IAM Insights with Custom Policies, you can easily build attribute-based access control to govern future IAM usage and prevent IAM drift.
Our goal with IAM Insights is to bring cloud policy enforcement and IAM security together in one platform to streamline cloud security as you grow your infrastructure.
Access to IAM Insights is now open to all teams on Bridgecrew and we’d love to get your feedback! Check it out and drop us a line with questions and thoughts on maintaining least-privileged IAM.
Get similar stories in your inbox weekly, for free
Share this story:

Bridgecrew
Bridgecrew is the cloud security platform for developers. By leveraging automation and delivering security-as-code, Bridgecrew empowers teams to find, fix, and prevent misconfigurations in deployed cloud resources and in infrastructure as code.
Latest stories
How ManageEngine Applications Manager Can Help Overcome Challenges In Kubernetes Monitoring
We tested ManageEngine Applications Manager to monitor different Kubernetes clusters. This post shares our review …
AIOps with Site24x7: Maximizing Efficiency at an Affordable Cost
In this post we'll dive deep into integrating AIOps in your business suing Site24x7 to …
A Review of Zoho ManageEngine
Zoho Corp., formerly known as AdventNet Inc., has established itself as a major player in …
Should I learn Java in 2023? A Practical Guide
Java is one of the most widely used programming languages in the world. It has …
The fastest way to ramp up on DevOps
You probably have been thinking of moving to DevOps or learning DevOps as a beginner. …
Why You Need a Blockchain Node Provider
In this article, we briefly cover the concept of blockchain nodes provider and explain why …
Top 5 Virtual desktop Provides in 2022
Here are the top 5 virtual desktop providers who offer a range of benefits such …
Why Your Business Should Connect Directly To Your Cloud
Today, companies make the most use of cloud technology regardless of their size and sector. …
7 Must-Watch DevSecOps Videos
Security is a crucial part of application development and DevSecOps makes it easy and continuous.The …