A quick introduction to CI/CD
CI/CD is one of the pillars of modern cloud native software development. It improves your …
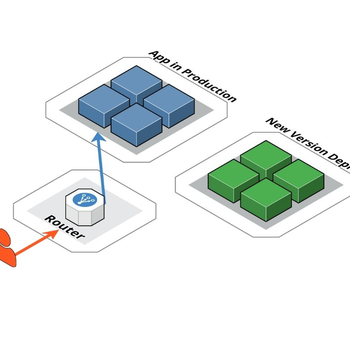
Blue-Green Deployment Explained
This article discusses what the blue-green deployment strategy is, its pros and cons, and its …
Popular Serverless Kubernetes Layer, Knative, Joins 1.0 Company: What to Expect?
The Knative team highlights the idea behind bridging the disparity between the maturity of the …
Python for DevOps
Python is a flexible and accessible programming language that makes various tasks such as scripting …
IAM Insights: Automated right-sizing with policy-as-code
AWS Identity and Access Management (IAM) is one of the few services at the backbone …